What is the Best Type of Security Awareness Training?
The number and types of security awareness training options can be staggering. In this article, we’ll walk you through some of the available options as well as the pros and cons of each.
When it comes to cybersecurity awareness training, a combination of training types should be chosen to effectively accommodate diverse learning styles and constraints people may have in terms of attendance. However, there is an abundance of choice, so let’s go over some of the more popular types below as well as their respective advantages and disadvantages.
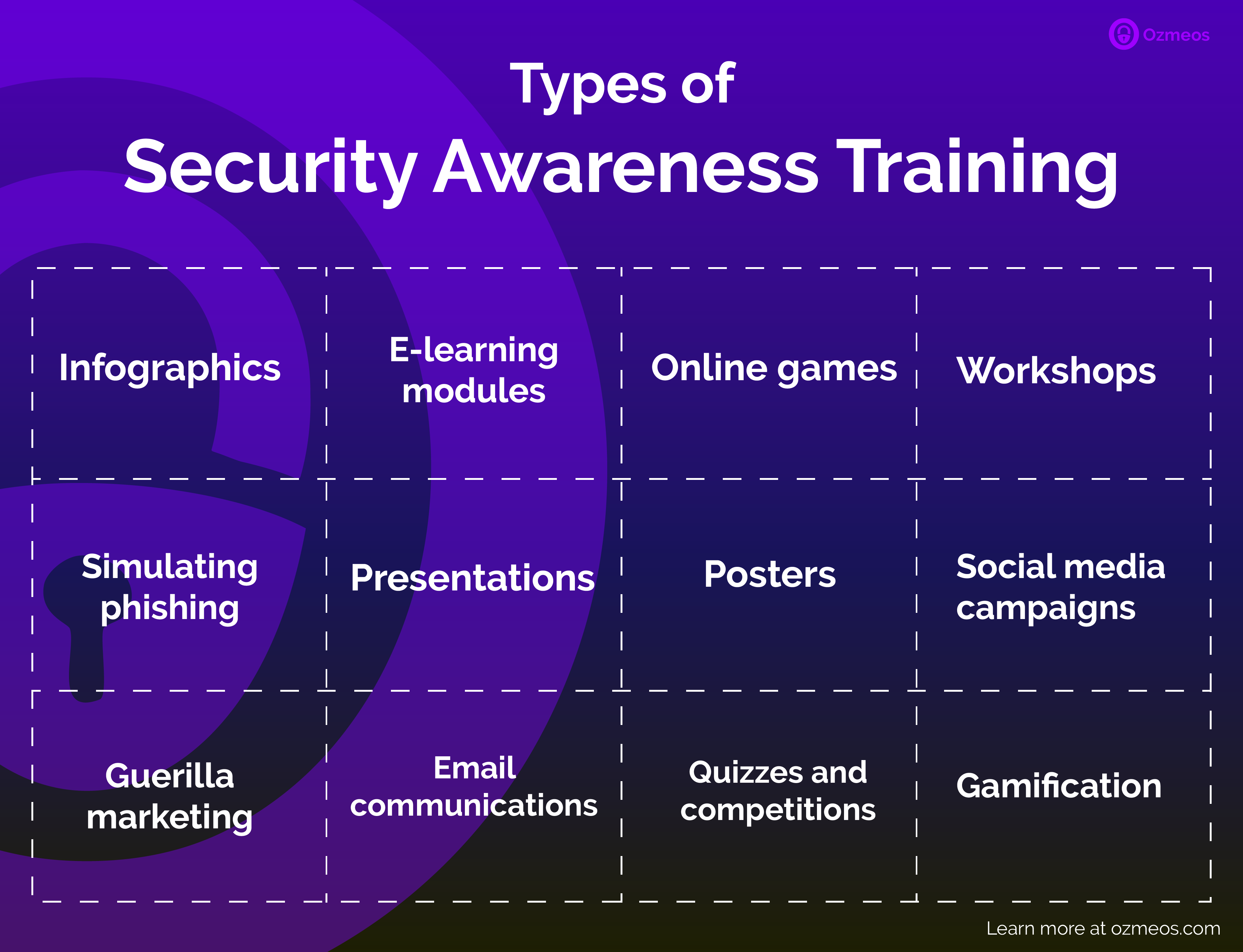
1. Online information security infographics
Infographics, provided they are showcased in an engaging and visual way, can be a way to easily capture the attention of end-users and showcase key messaging in an instant. They are easily accessible, and can be linked to from (or embedded in) emails and your intranet news pages. However, there might be limited room to show all your desired key messages, and they might not be able to capture your users’ attention for long. The benefit of infographics are that they are quicker and cheaper to source than other learning formats, meaning it is easier to have a regular variety of new materials and adapt to new threats quickly.
2. Online information security learning modules
Online learning modules may have a reputation of being tedious due to their often mandatory nature. To combat this perception, ensure you’ve chosen a topic that is relevant to, and likely to be enjoyed by, your audience. You should also consider whether you want the learning module to be in line with previous trainings you/your organization have to maintain consistency, or different in order to create a positive differentiation. Depending on the culture of your organization, a final quiz section could be appreciated to create an aspect of competition, however for others a simple pass/fail quiz section might be appreciated to ensure active learning has taken place. However, for some individuals these strict testing sections might create a slight element of stress and thus result in a negative infosec perception, so it could be strategic to incorporate these as lighter quiz elements throughout the training. In general, creating an engaging and entertaining module is preferable in order to capture genuine interest and ensure actual learning has taken place.
3. Online cybersecurity video games
A recent way of engaging end-users is through gamification. Although online games have the potential to deliver messaging in an entertaining way, you need to take care to not make these too difficult (limited learning will have been provided if the game ends if the user fails the first question!) or too tedious, as this will reduce the participation rate. Ideally, games with leaderboards can be a great way to create positive competition and enhance participation rates.
4. Static cybersecurity awareness posters
A potentially “old school” way of training, this non-digital format is generally a great supplement to other, more in-depth, types of training. These can often be sourced for free or relatively cheaply and they can often be re-used if the messaging is sufficiently general to remain relevant. However, with the rise of home-office setups, their reach might be limited. The poster format also has less space for detailed messaging, and are therefore best used as a supplement to other, more in-depth, training formats.
5. Email and intranet communication on security awareness
Often overlooked, email messaging can be a relevant method of providing key messaging, or raising awareness of other trainings, provided you have a well-thought out engaging text, graphics, and structure. It is important to both keep content both straight to the point, whilst ensuring your messaging is in line with your identified branding of your infosec team. In some cases, this is the primary way through which your end-users are able to ‘put a face’ to you, so it is worthwhile to invest time in crafting clear, consistent messaging.
6. Simulated phishing exercises
Fake phishing emails are an optimal way to teach users how to identify phishing attempts in a controlled environment. Make sure to positively reinforce those who are able to correctly identify the phishing attempts, as otherwise these trainings have a tendency to only educate those who click on the phishing link. Although typically associated with emails, it could be ideal to conduct these phishing scenarios through phone calls, text message, or in-person – to ensure all areas are covered.
7. In-person/online presentations on security awareness
Classic training presentations are a great way to showcase the people behind “cybersecurity”, creating a face to your infosec team. They give you an opportunity to showcase your personality and engage the learner through a variety of content types, engaging quiz tools and questions. It also lends itself well to an in-depth FAQ at the end of the training presentation. Depending on your audience, it can be advise to adapt your tone to generate a variety of emotions in the learner. Incorporating elements of humour, delight and surprise creates an engaging contrast and ensure attention is kept when you mention the more serious points, which are often those most important for the audience to retain. Whether online or in-person, ensure to encourage questions at the end of each session, and advertise a “call to action” for people to reach out to you if they are ever in need of anything. This ensures to lower the barrier to your team, making people more inclined to report suspicious behaviour or come forward with an incident, if needed.
8. In-person/online creative activities for cybersecurity awareness
Although online trainings, videos and infographics might be the first things that come in mind when considering cybersecurity awareness training, there is the potential to include other more creative activities that you are able to link to your key messages through statements made throughout the session or via closing statements. Sessions like these are great to get people on board who initially had no interest in cybersecurity. For example, an improv performance could showcase the risks of social engineering, or a martial arts workshop to learn the importance of the ability to anticipate opponents’ (or cyber criminals’!) moves. The sky is the limit, and provided you are able to insert your key messages, these could be ideal entrance activities to get people involved in infosec.
9. Tailored security awareness trainings
Different roles within an organization face distinct cybersecurity risks, and so it makes sense for trainings to be tailored to each group. Although tailored trainings would likely always be the ideal scenario, it is generally more costly in terms of human and financial resources. If you choose to do tailored training according to work functions, it is advisable to prioritise those with most risk associated with their role, while keeping a general training for all others.
10. “Guerrilla” training techniques for security awareness training
Guerrilla marketing involves surprise or unconventional interactions in order to promote their product or service. Depending on the culture of your organization, training and awareness techniques can indeed be done in a guerrilla fashion – making your cybersecurity training out of the ordinary to deliver a memorable “wow” factor. How about engaging your cafeteria for a secret menu item that needs to be decrypted? Or how about a goodie giveaway “spin the wheel” with cybersecurity quizzes or trivia? There is essentially no limit when it comes to creativity, however, depending on the impact these might be best seen as supplemental trainings.
Regardless of which kind of selected training type you choose to go for, you need to make sure you have robust communications and marketing strategies in place to ensure people are sufficiently engaged to click on or attend the dedicated trainings. In general, the best type of security training is one that caters to all learning types, i.e. a combination of the above, which is why we recommend a holistic approach through a dedicated awareness strategy and communication plan.